Threat exposure visualization for everyone
MITRE ATT&CK
Natively uses MITRE ATT&CK, ICS and ATLAS to visualize and quantify cyber risk.
DEFPOS® Rating
A tailored assessment of your organization’s defensive posture vs. the most relevant threats.
Actionable Guidance
Recommendations to strengthen weak points, prioritize spend and maximize improvements.
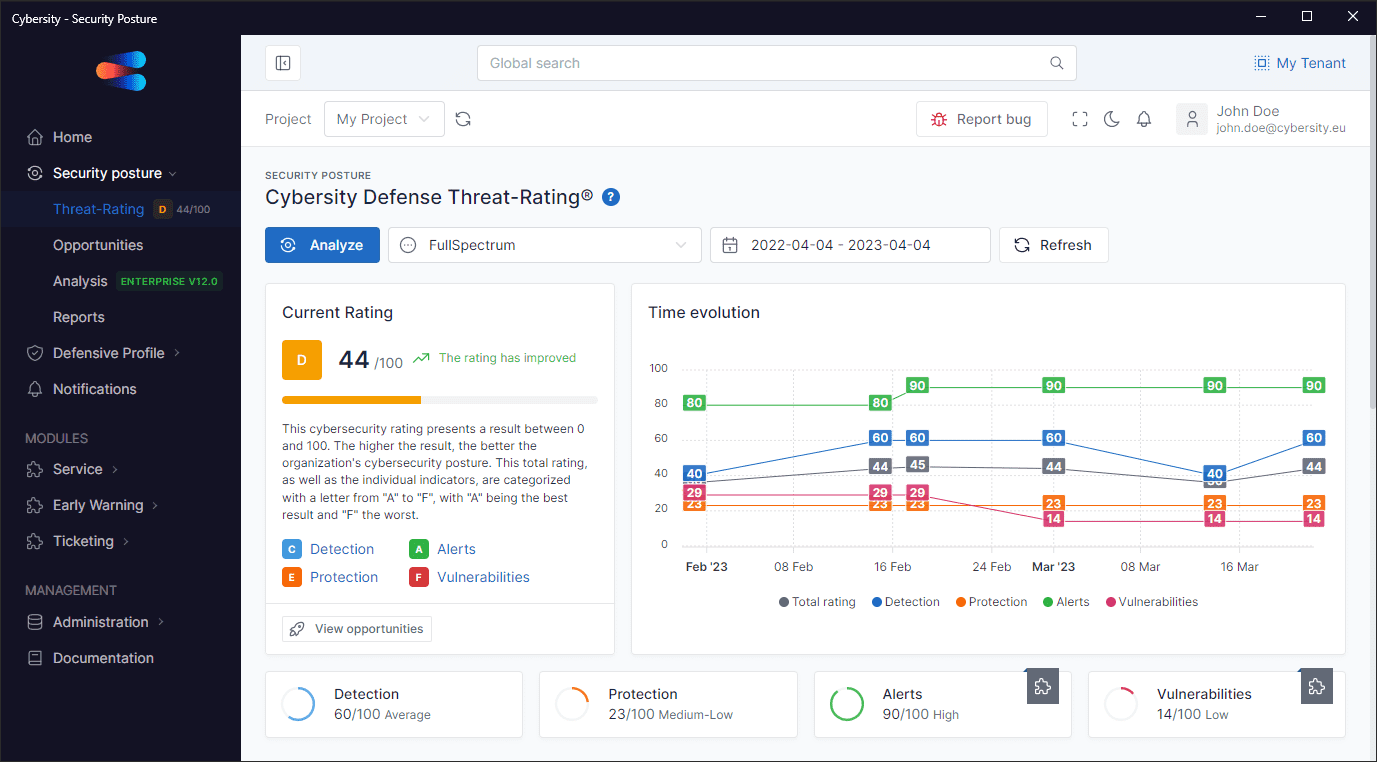
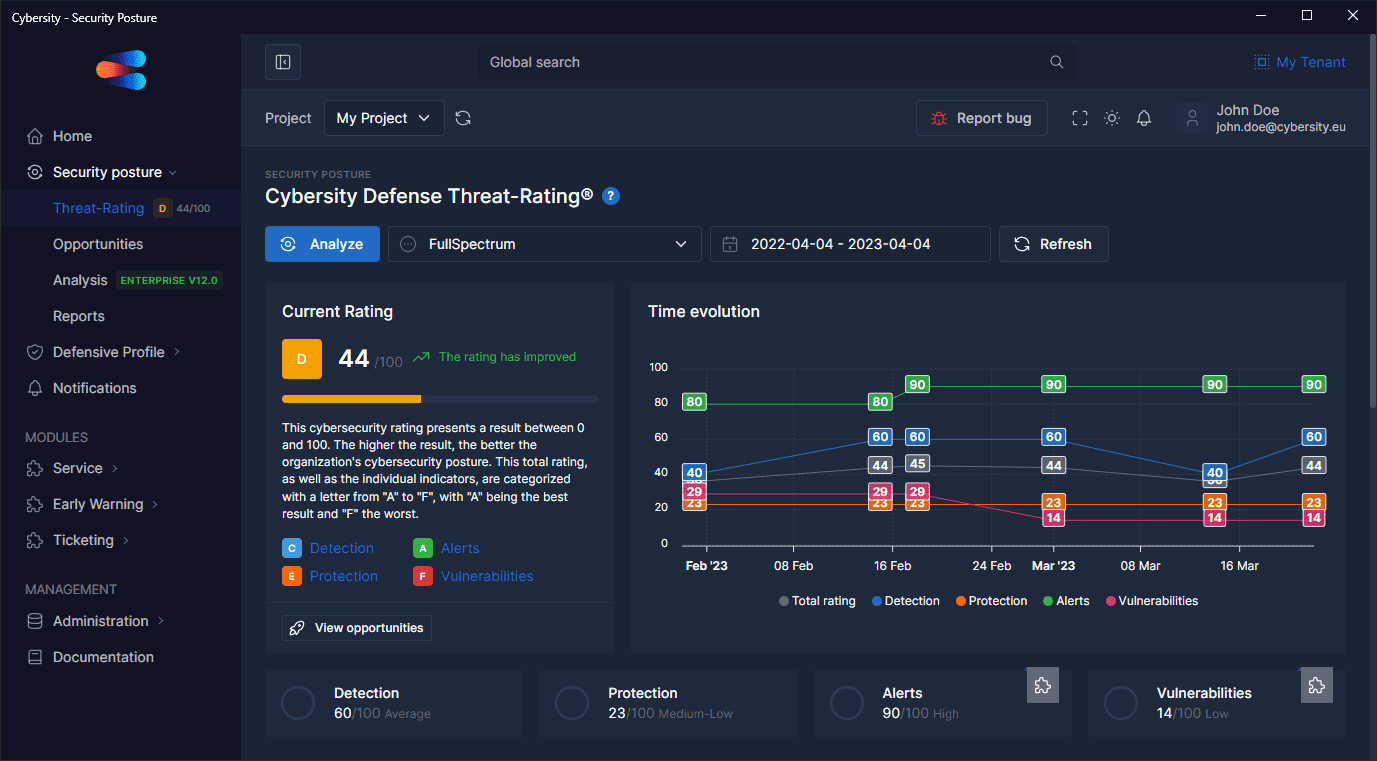
Cybersity DEFPOS® Rating
Your internal cybersecurity rating
Analyze your organization’s cybersecurity posture and obtain a rating tailored to multiple attack scenarios with prioritized improvement opportunities.
Dynamic Alerting
As threats evolve, Cybersity warns you when you need to update your defensive posture to adapt to the changing cyber threat landscape.
KPI Reporting
Use simple metrics to report your cyber performance and show it improving over time.
Features
Defensive profile
Defensive profile mapping, assessing detection and protection capabilities.
Base scenarios
Definition of any type of attack scenario to verify defense capabilities.
Threat-Rating
Verification of the organization's cybersecurity posture against multiple scenarios.
Opportunities
Prioritised recommendations to increase detection and protection capabilities.
Analysis
Advanced study using frameworks such as MITRE ATT&CK, MITRE ATLAS, MITRE CAR and others.
Reports
Download comprehensive reports on your organization's cybersecurity posture.
Integrations
Integration with ticketing systems and others to detect the types of threats received.
Early warning
Monitoring critical assets to detect vulnerabilities and complement the defensive profile.
Personalization
Complementing the defensive profile with the mapping of personalized security measures.
Latest posts
Discover the new version 1.3 of Cybersity
We are excited to share the latest update to Cybersity, with its new version 1.3. This release comes packed with...
Optimize your investment in industrial cybersecurity with Cybersity
Cybersity offers an innovative solution that reduces the complexity of cyber defense through a simple rating. This tool allows organizations...
CISO Challenge: Effectively Justifying Cybersecurity Needs in the Organization
In the complex world of cybersecurity, one of the most significant challenges facing CISOs (Chief Information Security Officers) is effectively...
Learn how Cybersity can help your organization
Request a Cybersity demo and our dedicated team will be in touch for a live demonstration of the product.